What does Vault let you do?
For years, the question of safe data storage has been widely discussed. Each of us has at least once puzzled over the question where to note passwords to keep them secret and never forget. Similarly, service providers and organizations owners worry about even more sensitive data. Hence, by installing Vault, you admit a need for data security, and by employing the tool, you make sure you secure, store, and tightly control access to your secrets and other sensitive data that might include tokens, passwords, certificates, encryption keys, etc.
Also, when deployed into Kubernetes, Vault allows even more. For example, the tool enables applications running in Kubernetes to store secrets from Vault by employing various secret engines and authentication methods or can serve as an encryption service for application to offload encryption needs. What is more, Vault can run on Kubernetes directly, hence, works with any other tool designed for Kubernetes.
Key Vault features and principles
Same to Terraform, Consul, and Nomad, other tools developed by HashiCorp, Vault targets a shift from static on-premise infrastructure to dynamic, multi-provider infrastructure, which changes significantly the approach to security. In static infrastructure, security relies on dedicated servers, static IP addresses, and a clear network perimeter. However, security in dynamic infrastructure is defined by ephemeral applications and servers, trusted sources of user and application identity, and software-based encryption. Thus, under Vault approach, we imply multiple clouds and private data centers without a clear network perimeter, low-trust networks in public clouds, and security enforced by identity, not IP address as it was in the traditional approach.
On top of that, even when a user wants to extend Vault, let’s say add a UI, there is no need to apply an external server, hence, secrets will not be passed through any additional server that might have low security level but will flow directly to Vault.
Undoubtedly, Vault key features bring a huge advantage to its users. With a view that access to sensitive data should be limited, the tool encompasses such features that allow it to be a sufficient data security solution that effectively prevents unauthorized disclosure and data breaches:
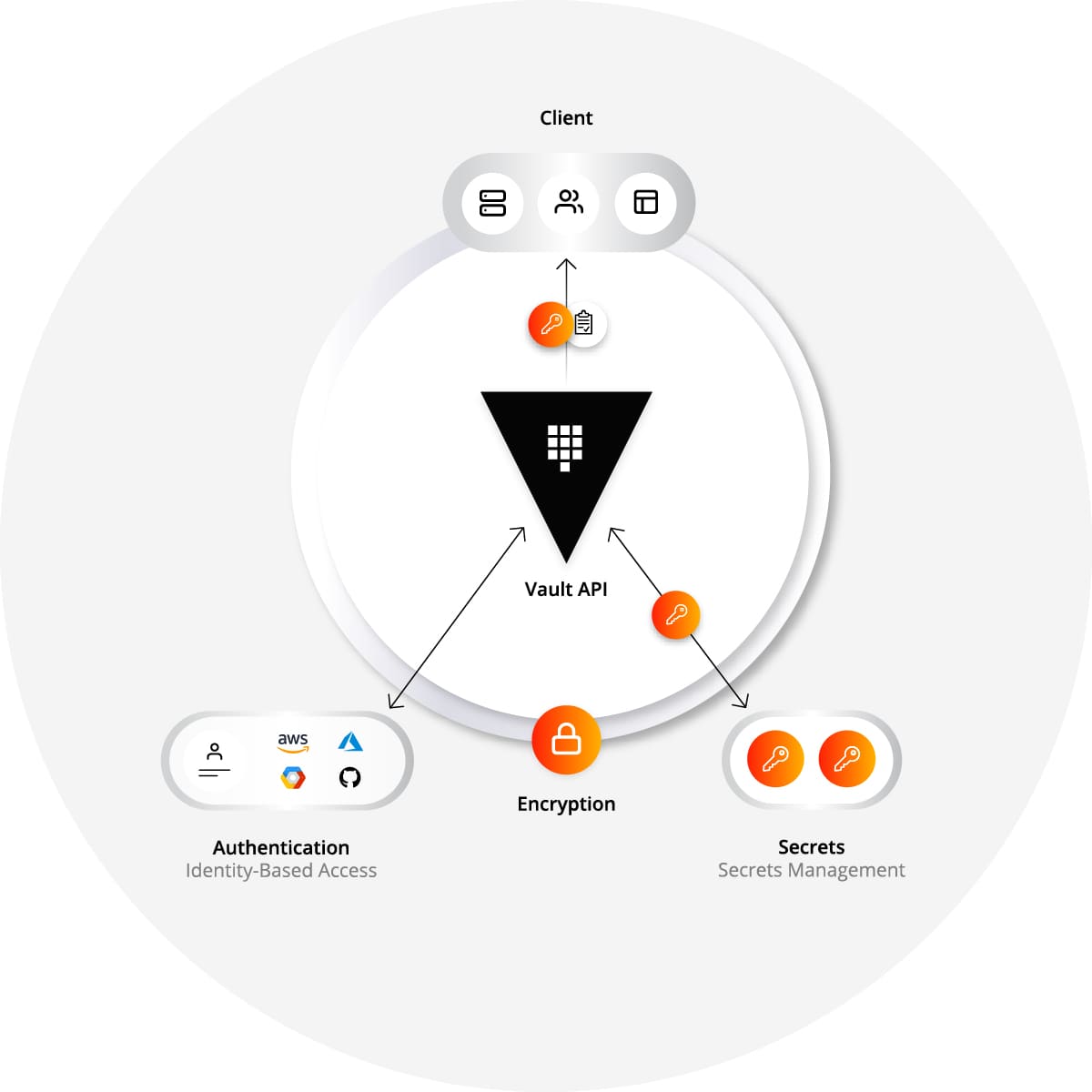
- Vault is API-driven, which allows the tool to efficiently encrypt, secure, and automate access to sensitive data.
- Vault employs identity plugins, which is done to smoothly integrate any trusted identity provider.
- Centralized workflow approach is used, which contributes significantly to safe secrets management and access.
- All secrets and data are stored in containers for convenience, and even if users obtain a container, it does not mean that they immediately gain access to information in it.
- All actions and requests are noted in the audit log.
Users can create Certificate Authority to be able to manage their own certificates within the infrastructure.
Why and when to apply
Indeed, Vault has one major mission - to protect the secrets from ‘bad guys’ and keep everything in order. Each user, though, interprets Vault’s functionality in a way that best satisfies particularly their needs. You, as the user Vault as a service, might be in search of a way to let your team access sensitive data and be always informed of actions taken on that data. Maybe, you just need to encrypt your secrets and simply store them safely. Thus, Vault is rather flexible in functions and is not limited to its main mission. Further, you can learn at least three ways to employ Vault.
Secrets management
Apparently, Vault was developed to address a particular challenge. With Vault solution, you can easily store, access, and deploy secrets across applications, systems, and infrastructure. The tool manages and enforces access to secrets and systems based on trusted sources of application and user identity. It encrypts data while at rest in the backend storage of the user's choice. The user can easily manage authorization and create time-based tokens for either automatic or manual secrets revocation. Besides, all kinds of user interaction (any changes, requests, views, etc) are noted in the detailed audit log, which undoubtedly boosts transparency and user experience.
Data encryption
Vault also lets resolve a challenge of application data encryption in low-trust networks. Though all application data should be encrypted, cryptography deployment and key management infrastructure is rather expensive and not cloud or multi-datacenter friendly. Now, however, data encryption is provided as a service by Vault with centralized key management. Encryption is API-driven and is done during transit or when at rest, which is rather convenient, while centralized workflow allows to keep application data secure.
Trusted identities
Traditional approach previously was unable to deal with multiple clouds, services, and systems each of which had their own identity providers. However, Vault approach enables management of various identities by merging them and using a unified ACL system (list of permissions in other words) to establish access to systems and secrets. With Vault, you can create and manage policies that authorize access control throughout your infrastructure and organization. You will for sure feel protected as to access a secret, multi-factor authentication approach is used to guarantee even more safety. Besides, you can manage trusted identities by grouping them to enable group-based access control.
Experience security with Quintagroup
Overall, Vault appears to be of maximum use in cases when data and secrets need to be safe and sound. We at Quintagroup have as well experienced the security provided by Vault. We have seen that the tool indeed addresses and successfully deals with the complexity and technical peculiarities of data security and secrets management. As Vault was designed to allow secure dynamic infrastructure across clouds and environments, it enables a safe shift from static infrastructure to the dynamic one, which, undoubtedly, entails numerous benefits for the end-users.
We are here to share our experience of working with Vault.